Introduction
Western Australian (WA) government entities use the Recruitment Advertisement Management System (RAMS) to manage staff recruitment and redeployments, and to record severance details. The public use the system to apply for WA government jobs. The system is externally hosted, and managed by a third-party vendor in a Software as a Service (SaaS) arrangement. It contains personal identifiable and sensitive information such as names, addresses, work history, qualifications, bank details and tax file numbers.
Conclusion
RAMS has successfully facilitated a significant number of recruitment processes since the application was implemented in 2003. However, we identified a number of opportunities to improve application governance. The Public Sector Commission (the Commission) has not undertaken or received independent assurance that key vendor managed information security controls are adequate and operating to ensure the confidentiality, integrity and availability of information in RAMS.
Further, the Commission cannot demonstrate it is monitoring and managing vendor compliance in accordance with the service level agreement and so may not be fully informed of any issues with service delivery or not meeting all users’ needs.
There is also a risk that insufficient business continuity planning could see an outage impacting recruitment activities across the whole of the WA government.
Poor user access management has the potential to expose personal and sensitive information to inappropriate access or misuse, particularly as the Commission has kept all information stored on the system since 2003.
Background
RAMS is a mandated whole of government e-recruitment solution. All relevant WA state entities must use the application to advertise vacancies, manage redeployments and record severances. Entities access the application via an internet administration portal. A separate portal is provided for data analysis and reporting. The public can view vacancies, create a profile and submit job applications online through multiple job boards (Figure 3).
In 2017-18, RAMS processed about 238,000 applications for almost 15,400 job advertisements. Currently, there are about 712,000 people with a job seeker profile in the application.
The vendor manages the underlying environment (network, storage, servers, virtualisation, operating systems, middleware, runtime, data and applications) and controls to protect the system.
The Commission retains ownership of the data and the risks to its confidentiality, integrity and availability (Figure 4). It is also responsible for monitoring delivery of service as per the SaaS contract arrangement.
| Security responsibility | Software (as a service) |
| Governance | Entity |
| Data | Entity and Vendor |
| Runtime | Vendor |
| Middleware | Vendor |
| Operating Systems | Vendor |
| Virtualisation | Vendor |
| Servers | Vendor |
| Storage | Vendor |
| Network | Vendor |
| Data Centres | Vendor |
Source: OAG based on RAMS contract and SaaS principles[1]
Figure 4: SaaS security responsibilities
The WA public sector has used RAMS since 2003. The most recent contract extension was awarded in April 2018 for 2 years. A service level agreement is in place that sets out expectations of service.
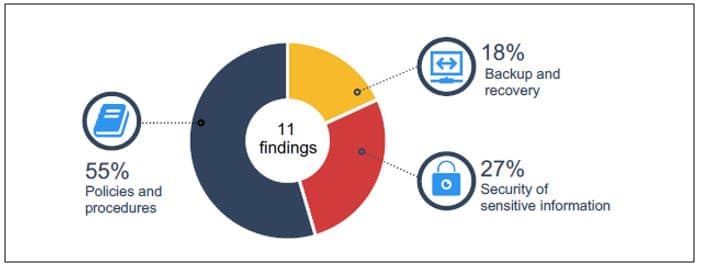
Audit findings
The Commission has not sought adequate assurance on vendor controls
The Commission has not undertaken or received independent assurance that key vendor managed information security controls are adequate and operating effectively. As a result, the Commission does not have assurance that information in RAMS is protected to ensure its confidentiality, integrity and availability.
We identified the following control deficiencies:
- Unsupported software – Some software components that underpin the application are no longer supported by the software vendors. In addition, 1 component has not had software updates applied that fix known security vulnerabilities. Unsupported and out–of-date software increases the risk of attackers using known vulnerabilities to gain access to sensitive information or disrupt systems.
- Disaster recovery not tested – The vendor has not performed a full disaster recovery test since 2015. The Commission cannot be certain that it can recover the application as required.
- Outdated technical specification documentation – The technical documentation describing the application does not reflect the current application environment. The Commission cannot be certain that all appropriate controls are in place to protect the application.
Lack of a risk assessment has led to inadequate information security requirements in the contract
The Commission did not assess the information security risks to the RAMS application and information at the time of contract or extensions. Without a formal risk assessment, the Commission is less likely to know if controls documented in the contract adequately address risks and vulnerabilities. In a SaaS environment, the customer does not directly manage the controls that protect information. Therefore, it is critical that controls are well defined in the service contract.
We found key terms and conditions for security of information are inadequately specified in the contract.
Weaknesses we identified include:
- No right to conduct security audits – There is no specific right for the Commission to conduct security audits of the RAMS environment. As a result, the Commission may have limited ability to verify security controls.
- No controls assurance – There is no requirement for the vendor to provide the Commission with third party assurance reports or certification that controls are in place and operating effectively. The Commission cannot be certain that RAMS and the information it holds are protected.
- Unspecified obligation to report data security breaches – The vendor’s obligation and process to report data security breaches to the Commission have not been specified. In addition, there are no defined penalties or indemnities for a security breach. Defining these requirements would allow the Commission to act in a timely fashion and, if necessary, recover costs in the event of a breach.
- Encryption not specified – Data encryption requirements to protect sensitive information in transit, at rest and stored on backups have not been specified. For example, the vendor does not encrypt backup tapes which are stored by a third party offsite. If the tapes are lost or stolen the information on them could be inappropriately accessed. The international standard for information security (ISO27002/2015) advises data owners to encrypt backup media where confidentiality is important.
- Unspecified data retention – Data retention requirements have not been specified. All information since 2003 has been retained in the system. This information is vulnerable to exposure if the application is compromised. Further, retaining all this information increases the risk that Australia’s Privacy Act 1988 and the European General Data Protection Regulation may be breached, which could result in infringements and reputational damage.
The contract should also be consistent with the State Records Office’s General Disposal Authority. This states that job applicant information should be disposed after 7 years for successful applicants and 1 year for unsuccessful applicants.
Inadequate access controls increase the risk of unauthorised access or misuse
We identified the following weaknesses in access controls to minimise the risk of unauthorised access:
- Ineffective user account management – The Commission does not have a policy or a procedure to manage entity user accounts, including highly privileged accounts. In addition, there is no process to routinely review user activity and their levels of access. There is an increased risk of unauthorised access to, or misuse of, information in the application.
Ineffective user account management may have contributed to the high number of enabled accounts (approximately 30,000). 26% of these (8,000 accounts) have never been used and 50% (15,000 accounts) have not been used in over 6 months.
- Weak password configuration – The ‘admin’ portal does not meet good practice requirements for password complexity and does not limit the re-use of passwords. In addition, multi-factor authentication, where user access is only granted after successful presentation of 2 or more pieces of information, is not required to access the application. This leaves the portal susceptible to password guessing attacks and unauthorised access to information.
- Unmanaged generic accounts – Fifty five entities use generic accounts to access the internet facing reporting portal and the password for the generic account is easy to guess. Generic accounts and passwords are shared by email and the Commission does not know who has been given this information. As the password is easy to guess and not changed on a regular basis, staff moving within or leaving an entity may retain access to the reporting portal, increasing the likelihood of unauthorised access and disclosure.
Inadequate business continuity arrangements
We identified the following weaknesses in the Commission’s business continuity arrangements that increase the risk that RAMS may not be restored in a timely manner after a disruption:
- Out of date business continuity plan – The Commission has not reviewed the RAMS Business Continuity Plan since 2014. Further, stakeholder entities’ critical functions, processes and their recovery objectives were not considered during the 2014 business impact analysis. There is an increased risk that RAMS may not operate adequately during an incident and key stakeholder recovery requirements have not been specified in the vendor service contract.
- Ineffective escrow management – A software escrow agreement is in place, but the vendor has not deposited the code, data or documentation as required by the contract. The Commission was not aware of this since it had not verified the deposits to confirm that RAMS can be recovered from escrow. Without escrow deposits, the Commission will not be able to recover and continue the use of RAMS if the vendor can no longer provide the services.
A software escrow helps protect all parties in a software license by having a third party (escrow agent) hold application source code, data and documentation. It ensures the Commission has access to a copy of the system, under certain contractual conditions.
Vendor compliance has not been well monitored to ensure RAMS meets entities’ needs
We identified weaknesses in how the Commission manages the service level agreement (SLA). These increase the risk that the Commission will not receive the contracted services, or be aware of issues with the vendor’s service delivery.
In particular, the Commission has not implemented key requirements of the SLA to manage the contracted service delivery. For example, the Commission has not:
- held annual contract review and periodic contract management meetings
- established, or allocated, a governance body to support forward planning and provide feedback on vendor performance
- conducted annual user satisfaction surveys since 2013
- received application backup reports and capacity management plans from the vendor.
We note that the Commission does hold quarterly and ad hoc meetings with the vendor. The Commission informed us that the 3rd quarter meeting is considered to be the annual review of the contract. However, we found no documentary evidence of an annual contract or SLA review in our examination of the most recent 3rd quarter meeting agenda or minutes.
Important application management processes could be improved to reduce the risk of unplanned system downtime
The Commission and vendor have not adequately documented, and do not routinely follow, change and incident management processes to manage issues with the application (e.g. incidents). Inadequate change and incident management can lead to unplanned system downtime and recurring issues. We identified the following weaknesses:
- Changes are not properly managed – Change management documentation is unclear and inconsistent. In addition, the vendor had not provided detailed change process documentation as required by the SLA. We tested 2 changes which identified that:
- the formal contract change template is not used
- written confirmation of regression testing, to confirm changes have not negatively affected existing functions, and user acceptance testing is not performed.
- Incidents are not properly recorded, classified and analysed – The Commission does not record incidents and service requests in an appropriate service desk tool, increasing the risk that incidents may not be resolved in a timely manner.
We note that the vendor does provide the Commission with incident volume reports. However, we found that incidents are not classified to allow trend analysis, and there is no documented process for identifying the root cause of recurring incidents. There is an increased risk that recurring incidents may not be identified and addressed.
Recommendations
The Commission should:
- implement a risk assurance framework for SaaS arrangements and conduct a risk assessment of the RAMS application and information. Update contractual terms based on identified risks
Commission response: Agreed
Implementation timeframe: by December 2019 - implement appropriate mechanisms and processes to manage and monitor SLA contractual obligations
Commission response: Agreed
Implementation timeframe: by December 2019 - establish a suitable mechanism for obtaining feedback from stakeholders in key entities
Commission response: Agreed
Implementation timeframe: by July 2019 - implement appropriate user account management practices and communicate these to all entities
Commission response: Agreed
Implementation timeframe: by October 2019 - review and update the RAMS Business Continuity Plan based on an appropriate Business Impact Analysis involving key stakeholders, and update contractual availability requirements, if required.
Commission response: Agreed
Implementation timeframe: by December 2019
Response from the Public Sector Commission
The Commission notes the feedback and recommendations provided and undertakes to implement these recommendations.
The current whole-of-government e-recruitment system (RAMS) has had no security breaches since its inception in 2003. The Commission is confident that users’ information is protected to ensure its confidentiality, integrity and availability.
The information provided in the audit will assist the Commission in enhancing the management of this contract, and will guide its future contractual requirements relating to information technology security as well as its auditing and application control requirements.
[1] https://cloudsecurityalliance.org/download/security-guidance-v4/